[Image above] With this new way of eavesdropping, you’ll want to make sure you close the curtains at night. Credit: Pixabay (person listening and lightbulbs)
In our digital world, privacy and security are mostly an illusion.
Many of the security measures we take for granted, such as antivirus software and photo ID checks, are just security theater, or measures that give us the sense of security without actually providing any. And recent investigative exposés on social media giants—particularly Facebook—have opened users’ eyes to how little they control their personal data.
Recently, the question of privacy gained new urgency as Black Lives Matter protests shined a light on the potential problems and dangers of facial recognition technologies. But even with this heightened scrutiny, the possibility of companies enacting sweeping changes to data security and privacy are slim.
And so I find it interesting that during these tumultuous times I would come across a new technique for eavesdropping—a technique that costs less than $1,000 and works from hundreds of feet away.
Lamphone: Lightbulb vibrations provide real-time listening
In early June, researchers from Ben-Gurion University of the Negev and the Weizmann Institute of Science in Israel revealed a new technique for long-distance eavesdropping called “lamphone.”
Lamphone is based on the knowledge that soundwaves can cause a hanging lightbulb to move ever so slightly (a millidegree vibration). By observing these vibrations with an electro-optical sensor, the fluctuations in light that result from the movement can be converted into an electronic signal—which an audio recovery algorithm then uses to reconstruct the original sound.
In a paper describing the technique, the researchers explain the advantages lamphone offers over other eavesdropping techniques.
“[Other eavesdropping techniques that analyze side effects of soundwaves on nearby objects] are limited in one of the following ways: they (1) cannot be applied in real time (e.g., Visual Microphone), (2) are not external, requiring the attacker to compromise a device with malware (e.g., Gyrophone), or (3) are not passive, requiring the attacker to direct a laser beam at an object (e.g., laser microphone),” they write.
In contrast, lamphone takes place in real time, does not require a compromised device, and is passive (does not require a laser beam).
To observe a hanging lightbulb from far away, the researchers paired the electro-optical sensor with a telescope. In experiments, they successfully reproduced songs and snippets of speech from 25 meters (82 feet) away—which you can listen to at the 3-minute mark in the video below.
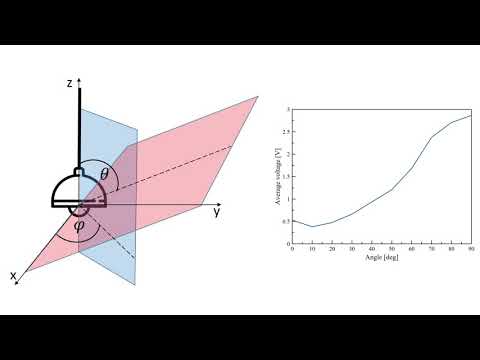
Credit: Cyber Security Labs @ Ben Gurion University, YouTube
Though the findings of this study may be uncomfortable—do the results equip spies with new tools?—the researchers emphasize they pursued the study to make clear to people on both sides of surveillance what is possible.
“We want to raise the awareness of this kind of attack vector. We’re not in the game of providing tools,” Ben Nassi, security researcher at Ben-Gurion, says in a Wired article.
In line with this goal, they included a section on countermeasures within the paper, such as reducing the amount of light a bulb emits and limiting the bulb’s vibration.
In the future, the researchers note it could be interesting to see if sound can be recovered from other light sources. “One interesting example is to examine whether it is possible to recover sound from decorative LED flowers instead of a light bulb,” they write.
Author
Lisa McDonald
CTT Categories
- Material Innovations